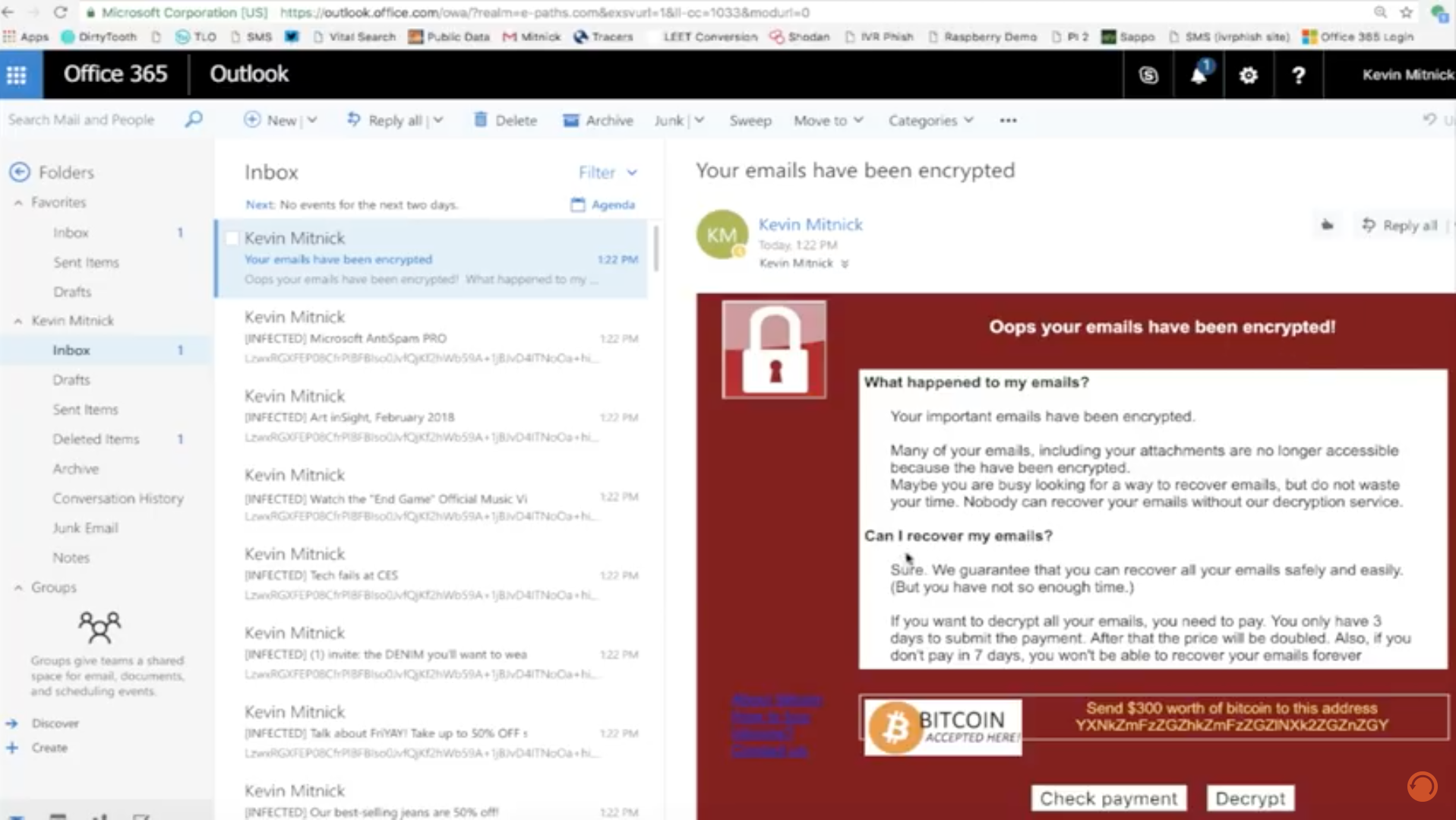
This one is really scary and is leaving our team very concerned. A new white hat hacker has discovered a way to create "ransomcloud" where any cloud service you store data in can potentially be encrypted and your data held for ransom.
We have heard from many companies we have spoken to that they are "safe" because their data is "in the cloud". First of all, this isn't exactly true, while the cloud is redundant and secure, there are many security instances you have to consider when storing data in the cloud.
This new ransomware in the cloud adds a whole new level of complexity. Where as conventional Ransomware encrypts files on your computer, network, server and other networked devices, Ransomware in the cloud encrypts things like email, cloud file services (like dropbox/box/onedrive/google drive), and potentially other web databases.
You can see a video created by the guys at KnowBe4 on their proof of concept.
So what should you do about this?
- Educate your employees, they play a pivotal role on keeping your company safe, because in essence they hold a big key to the kingdom because they have access to your email, computers and networks. (We even host free employee training for local businesses: www.creativeit.com/employeetraining/)
- Setup email anti-spam and anti-virus protection. Services that can scan for and block suspicious emails and their attachments from ever reaching your employees. We use a product internally and with our clients that blocks this unwanted spam.
- Use an Advanced Anti Virus product that not only scans for viruses but is advanced enough to detect anomalies in software and paterns, we cover this in our Security Series: www.creativeit.com/cybercrimeantivirus/
- Backup Backup Backup... Even if it is a cloud service make sure you have a backup that is holds multiple versions, backs up often, and does not overwrite older versions. This way you can potentially restore in the event of something like this.